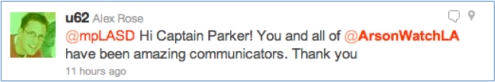
The Massachusetts Western Region Homeland Security Advisory Council, or WRHSAC, sponsored a social media training event Friday, September 21, 2012 in Northampton, MA. Below is a summary of the event, including Tweets from the tag #WMASMEM. If you attended please be sure to fill in the comment form at the end of this post.
The agenda was packed with information from the perspective of the community members themselves, and facilitators Jeff Phillips and Kim Stephens led the way. We started the day with a “check-in” regarding what attendees thought was the biggest obstacle for their use of social media. Each table reported one item they felt was the biggest impediment. They came up with the list below, and interestingly, 3 different groups thought “time” or resources was the biggest issue.
- comfort using tools- legality (how far does it go? where does it end)
- governance
- SOPs (message control, etc)
- time to keep it updated – keeping current & fresh (resources)
- social media policies are restrictive
- clarity and consistency – message control
- ensuring consumers/citizens are aware
- time to do it all
- time (how do we control the incoming traffic – to be responsive)
- crowdsourcing data, finding out what’s out there
- not all people have access to tools but would like to see what’s on the social platforms
- how do people differentiate their between their various roles in their lives (e.g. selectman and employee).
The attendees were reminded that the facilitators had established a training blog titled “Western Mass SMEM.” This blog site has many resources for the participants to use well after the day of the workshop, including modules on specific topics as well as “lay-of-the-land” maps.
The maps have links to all the social media sites the facilitators could find by emergency service organizations in the Western Region including public health, NWS, law enforcement, emergency management and city government. There are two categories of maps, county versus State and Regional. The State and Regional maps include applicable agencies such as MEMA. Why is doing a “lay-of-the-land” an important step? Read Module 18 for the details about why organizations should understand who else is Tweeting and posting.
Legality: What public organizations need to know.
The first presentation of the day was given by Linda Hamel, General Council for the state of Massachusetts, Information Technology Division. Her talk was titled Three aspects of Social Media Use for Public Sector Employees. This informative presentation had many great take-aways including: letting participants know that organizations have to be very careful about deleting people’s comments on government sponsored Facebook pages or blogs because of first amendment free speech protections; that staff should be informed about what behavior is expected on or off government social sites, such as on their personal Facebook page; and what kinds of behavior on social sites can lead to disciplinary actions.
Fire, Police and Emergency Managers Discuss Use of Social Media
The first panel of the day was quite lively and included Chief Wynn, Pittsfield Police Department; Bob Labrie, Goshen Fire; and Ryan Quimby, Town of East Longmeadow. They discussed their use of social media and told some great stories about how they use these tools to reach their communities before, during and after a crisis.
Some interesting take-aways: FB can and has been used catch criminials; social networks can be used to inform the public very quickly of what is occurring–well before traditional media goes to press; by monitoring social sites organizations can determine what the public is saying about them–good or bad. Chief Wynn stated–the public is talking about your organization anyway, if you are also on social networks at least you are able to see it and respond. This seemed to resonate with participants. Another kind of funny take away–cute pictures increase traffic to your site: people love babies and animals and especially baby animals!
One of the concerns from the audience was about rude comments on their organization’s page. Facilitator Kim Stephens mentioned the case study posted on the blog that discusses what can happen when people post irrational or inflammatory comments. That post can be found here: Module 10.
Question: How many minutes a day do you spend on posting to your Facebook page? Answer from Bob Labrie–30 minutes or so, which includes crafting the post.
Social Media for Professional Connections: #SMEMChat
Learning to use Twitter was part of the day’s activities and included a discussion on the use of the network to connect to other professionals.
With this idea in mind, the workshop attendees joined the #smemchat on Twitter, which takes place every Friday 1230 EST. The chats are often joined by emergency managers from all over the United States. Quite a few people were testing the water with this experience.
https://twitter.com/bkdelong/status/249200239867731968
Some of the more experienced Twitter users in the crowd really dove into the chat discussion, which was about dealing with rumors on social platforms during a disaster event. See the storify of the chat here and a Tweetdoc version here. (Tweetdoc is document that brings together all the tweets from a particular event or search term.)
Most of the exercise involved just learning to use Twitter in a quickly moving environment, such as a chat. These chats make a good no-fail exercise each week. One of the things participants discussed afterwards was that it was “kind of hard” to keep up, illustrating the need for more practice.
Social Media and Public Health Communications
The public health session began with a video by Dartmouth-Hitchcock Hospitals. The 3 minute YouTube video is used to train employees about their social media policy.
Panelists included Sam Brody, Representative from Cooley Dickinson Hospital; and Steven Jay Cohen, also of Cooley Dickinson and John Jacob of the Massachusetts Department of Public Health.
John Jacob told the audience that DPH primarily uses a blog and a Twitter account to reach citizens, they currently do not have a Facebook page. The blog allows them to post stories and information in a more flexible format than the agency website. The blog also allows for interaction with the public via the comments section. See this module for more information about blogging: Module 19: Blogging for Public Health and Safety Organizations.
One interesting problem the private sector hospital representatives brought up was the issue they are encountering regarding the balance between emergency information versus “brand” information. They are still considering whether or not they should they post from the same account or establish a new one just for emergency-type messages.
https://twitter.com/_JoLane/status/249222741348212737
https://twitter.com/_JoLane/status/249221883382358016
One great point made by Mr. Cohen was that the hospital has to be careful when repeating messages created by others or “ReTweeting.” They want to ensure that message is verified information because the second they repeat it, it can be viewed as an endorsement of that content. Public sector organizations should also take this into consideration.
https://twitter.com/_JoLane/status/249223003068583936
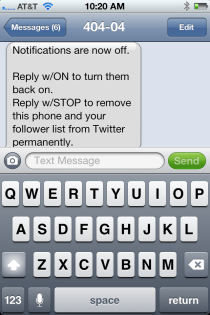
40404
The participants learned how to use Twittter’s SMS texting capability, specifically the “fast follow” feature using 40404. More information about this capability can be found in Module 17. We learned that in order to follow someone (or an organization) via SMS on their smart or even “dumb” phone, users simply text to 40404 and then “Follow [username].” If you text the word “stop” to 40404 it turns off all text notifications. Users could also type “unfollow [username]” to remove the notifications from that specific person or organization.
Volunteers and Donations Management
The last panel of the day addressed how spontaneous volunteers and organizations use social media in a crisis. The panel included Morgan O’Neill of Recovers.org; Wendy DeShais, a volunteer from Monson, MA; and a member of the local media, Peter Chilton, the social media director for New England Public Radio, located on the UMass campus.
We began the session by viewing a Ted Talk that included Morgan O’Neill and her sister Caitria. In the talk they discuss how they organized volunteers in Monson using both Facebook as well as “post-its” after the June 1, 2011 tornado event. Morgan elaborated on the talk by telling the story about how after posting a need on Facebook not only would the requested item show up–but often x10, requiring a quick retraction: “We no longer need freezers!”
Wendy pointed out the necessity of keeping up with all of volunteer activities–spontaneous or not.
Mr. Chilton addressed how improvements could be made between the media and officials involved in getting out emergency messages.
What Now?
Those of you that attended the workshop, and used some of these tools for the first time, might be wondering what you can do to keep up both your new-found skills as well as the connections you made during the day. We have several suggestions:
- Follow and friend each other’s new social presence(s) on both Facebook and Twitter.
- Connect to the WRHSAC’s Facebook pages and Twitter accounts: the WRHSAC Facebook page (with the intended audience of first responders) and their Western Mass Ready Facebook Page. Also connect to the Western Mass SMEM page–which was created for attendees and regional constituents to use as a place to both try things out and share best practices.
- Connect to each other on Twitter via the #WMASMEM hashtag–maybe even pick a time to have your own regional chats. If you are still unsure about Twitter revisit Module 11: Twitter Basics.
- Connect to other regional Twitter users that have been aggregated here: https://twitter.com/i/#!/JSPhillips2/wrhsac/members. This Twitter List was created by Jeff Phillips and has 109 members including the new Twitter users from the workshop–Jeff was adding new accounts as they were created.
- Practice!!!!!!
Thanks to everyone who participated and presented. It was a very successful day!